east-tec Eraser offers you the flexibility of choosing different wiping methods for erasing each module independently of one another (Privacy Guard, Erase Files & Folders, Erase Deleted Data, Media Wiper). There are 14 wiping methods to choose from and the built-in slider selector makes it very easy to pick the one that best suits your needs in each module. Different methods work at different speed and security level and are therefore recommended for different scenarios. After selecting a particular wiping method in a module, east-tec Eraser applies it to each erasure action in the given module. Below, we are going to go through each module in relation to what wiping method is recommended for erasing them and show you how to use the slider selector to choose the right method.
Privacy Guard
The Privacy Guard covers the following important sensitive areas: Applications, Browsers, News & Emails Readers, Peer2Peer, Security, Windows 8 Apps, Windows, Custom. The recommended practice to keep those areas secure is to run, or schedule to run, a daily wipe overnight with the Stop Software Recovery Tools method. This is a quick, yet secure method that makes sure that hackers and other third parties using software recovery tools can't restore data you have wiped with it. To select it follow the simple steps below:
-
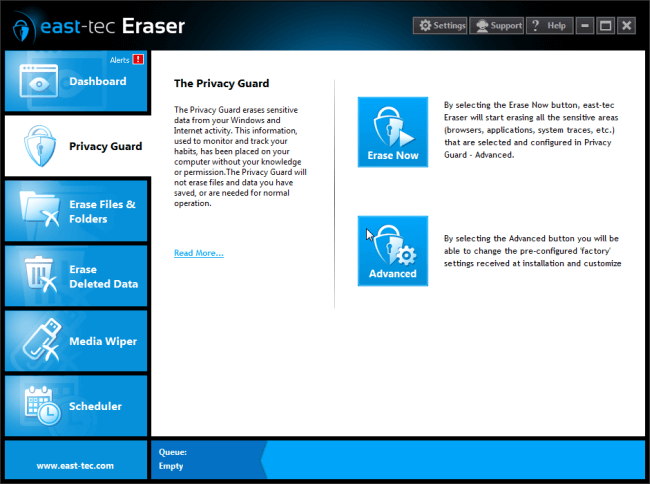
Run east-tec Eraser, select Privacy Guard, and click Advanced.
-
Select any categories (Browsers, Applications, etc) and with your mouse, move the slider selector to the 4th position on the horizontal method list to get the Stop Software Recovery Tools method.
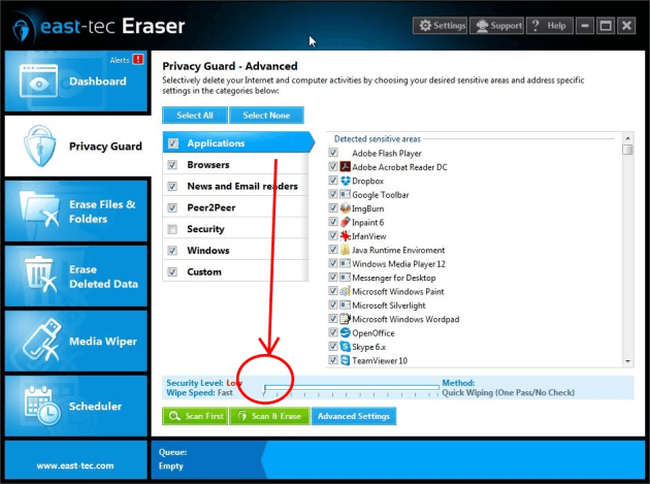
Erase Files & Folders
To securely delete your sensitive files and folders you can use the Stop Software Recovery Tools method, again. However, if you prefer to protect your data even from hardware recovery tools, go for the Gutmann 35 pass method, which is a slow, but super-safe standard. You can find it at the right-hand side end of the method list.
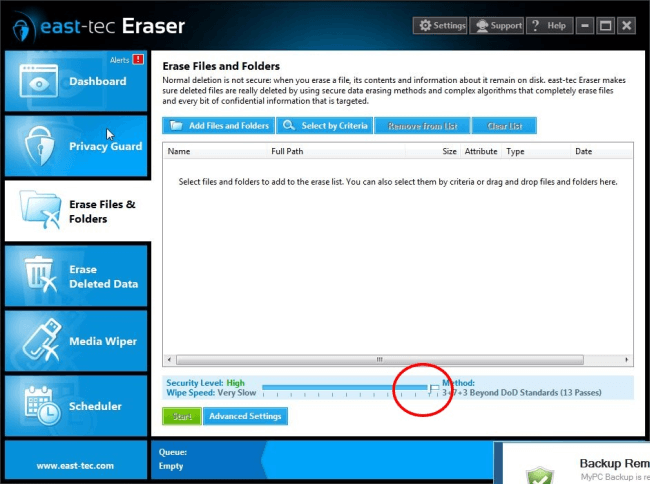
Erase Deleted Data
Data you have previously deleted using the default delete function in Windows is very likely to be still on your hard drive. Normal Windows deletion only removes file references from directories, but leaves the actual file content on your computer. To make sure that such sensitive remains can't be recovered by unauthorized parties, run the 3+7+3 Beyond DoD Standard method. This is a slow, but very secure method for thoroughly wiping the free space of your hard drive where previously deleted data remains reside. To select the 3+7+3 Beyond DoD Standard method, move the slider to the one before last position on the right-hand side.
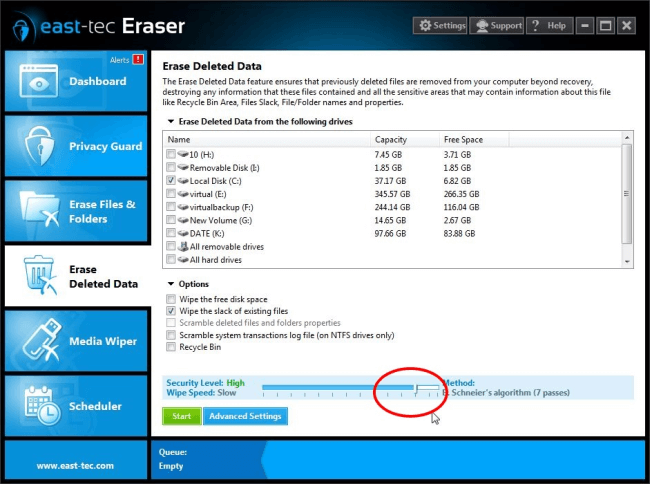
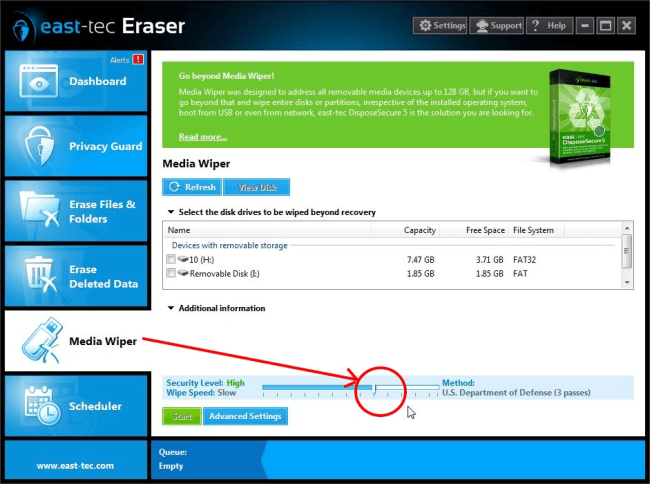
Media Wiper
east-tec Eraser lets you securely erase data from removable media devices attached to your computer. Since the data storage mechanism of media devices are different than that of computer hard drives, and to take wear leveling into account, here we have two recommendations for you:
-
To stay protected against software recovery applications, select the Stop Software Recovery Tools method and run a wipe with it.
-
To stay protected against hardware recovery tools, run the Gutmann 35 pass method once to erase the device. This practice makes sure that even hardware recovery tools won't be able to recover data that was stored on the device prior to the wiping process. You can find the Gutmann 35 pass method at the right-hand side end of the list.
Take your time to get familiar with the best practices and methods recommended in this article. Using the slider selector lets you save time and increase efficiency by choosing wiping methods that best suit each erasure action you want east-tec Eraser to perform.
