
Mother's Day is just around the corner so most of us are already busy looking up gift ideas online. As long as we only look, things are less risky. But if you have already found the gift you want to give your Mom in a few days time, stop for a minute before you go to checkout. Let's offer you some...
3 min read
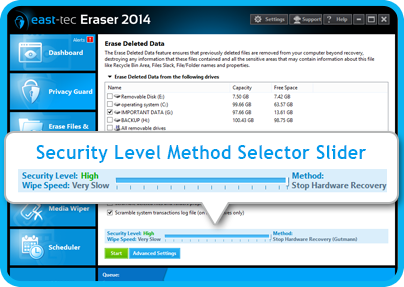
There are numerous data wipe standards for the secure removal of sensitive information from PC hard drives and removable data storage devices. east-tec Eraser offers you 14 of them. In this article we would like to recommend you wipe methods for different privacy scenarios and tell you what...
4 min read

Since the web is full of posts about the Heartbleed bug (CVE-2014-0160) - a vulnerability in the Open SSL that secures sensitive information online - we thought it was necessary to inform our customers that neither the East-Tec site, nor our financial transaction partner sites, Avangate, and...
2 min read

No matter how much we want to keep major holidays, such as, Easter, a carefree, intimate family affair, in hacker-world there is no stopping to honor those events. Just on the contrary. Cyber criminals often increase their activities before and during holidays, knowing that this is when most...
3 min read
Most PC users are conscious of privacy issues associated with their browsing history. But history isn't the only sensitive trace your browser logs about your activities. Cookies, cache, download history, form data, session store, saved passwords, etc, can also compromise your privacy a great deal,...
5 min read

Cloud backup services have become extremely popular in the last few years. Long gone are the days when we needed to email ourselves a file, or carry it on a flash drive, if we wanted to use it on another device. Sharing files with others, for instance, a favorite video with a friend, can also be...
4 min read