I'm sorry to be the bearer of bad news, but when you clear your history to keep your browsing activities confidential, it's like moving a folder full of confidential documents from your desk into the desk's drawer. Even though the folder is gone from the direct view of unwanted people, but the documents still exist and can easily be found with a bit of extra effort.
In technical terms, your deleted browsing history can be recovered by unauthorized parties, even after you cleared them. Why is it so? Let's explore how Windows deletes confidential information and you'll know the answer in a short while.
But first, let's have a look at what browsing history actually is.
Your browsing history is made up of various items, such as, site URLs, cookies, cache files, download list, search history and so on. The type of files we need to focus on now is the cache files, because they are easy to recover and once recovered, they can reveal unauthorized parties basically everything about your Internet activities.
So what are the cache files and what do they do? Let's say you visit www.amazon.com for the very first time. The site has a distinctive brand logo, a checkout cart, a sign-in box and many other items that remain unchanged anytime you visit the site. The site also displays hundreds of products that are likely to stay on the site for some, or a long time to come. The way your browser is "thinking" is this: Why don't we save the permanent page elements to the computer so we don't need to download them again and again from the remote Amazon server when the guy returns to the site?
That's a really nice feature that speeds up browsing a great deal. However, please keep in mind that your browser caches everything it encounters just in case it needs to use that item again, be it a logo, an image, a photo, a video, a podcast, a site URL and so on. So after a while the cache folder turns into a digital travel diary that has a record of every websites you have ever visited and the activities you have performed on those sites.
Like I said, your browsing history includes the cache files. Now, the problem is that when you "delete" a file in Windows (it doesn't matter if it's a photo, a financial plan, or a cache file), the operating system doesn't bother shredding the sensitive information (overwriting it with random data). To save time and resource, it simply removes the file's reference from the directories (that's why your deleted browsing history seems to be gone) and moves the actual information contained in the file to a special area, called free space, on your computer's hard drive where it will be overwritten by new files over time. However, the problem is that Windows employs a user-independent pattern to overwrite deleted files so the overwriting can take weeks, months, or even years!
Since the confidential history files are actually not gone from your computer after deletion, they can be accessed and recovered by unauthorized parties using free file recovery tools available on the web.
Let's say your laptop gets stolen. To demonstrate what confidential information could be recovered from your stolen laptop, I cleared my browsing history on my own computer and run a file recovery tool on it (so now my computer represents your laptop). Here is what the guy could find out about my online activities:
Browsing history
As you can see, these excerpts from a recovered history log clearly show what sites I recently visited and even the date/time of visiting.
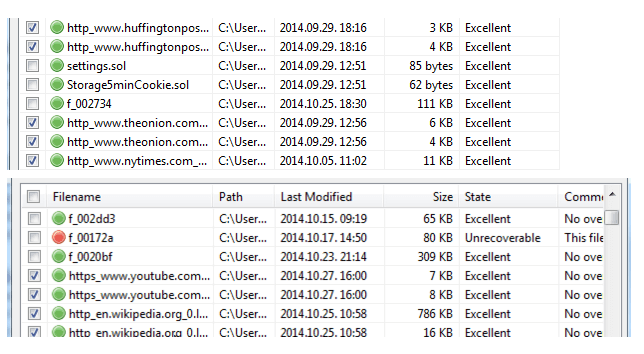
And it's not only general site URLs that can be recovered, but also the exact pages I visited on a particular site. A few examples from the recovered History Provider Cache:
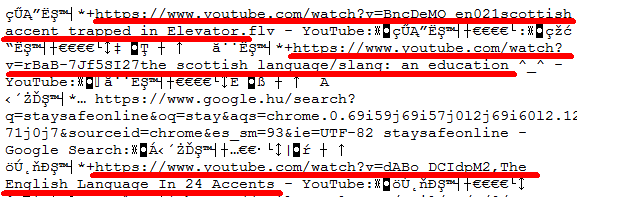
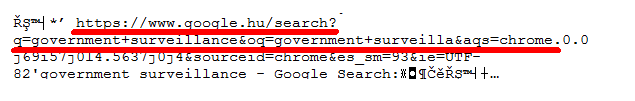
The recovered History Provider Cache also has records of search terms I entered into the search box in Chrome:
Images/photos/videos
The hacker could also recover what images/photos I viewed on various websites. Recovered images and photos have weird names, like the one circled below, because, like I said, after deletion the file reference is gone. Nevertheless, the confidential files are still there to be recovered:
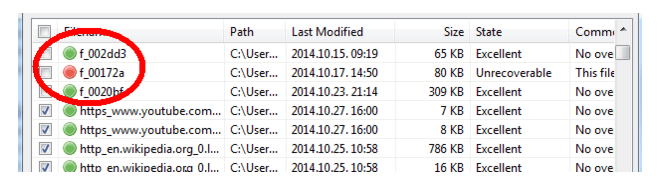
If the hacker opens these files with a photo manager, or multimedia application, such as, Windows Photo Gallery, RealPlayer, Picasa, etc, he can discover what photos/images I viewed on various sites. A few examples from my recovered history:
- Photos of items I browsed/purchased (Amazon, eBay, etc.)
- Photos I viewed (National Geographic, Playboy, Huffington Post, etc)
- Thumbnails of sites I visited
- Images/photos I uploaded to/downloaded from the web (Google Docs, Facebook, etc)
- Screenshots I made
- Images created for and pix used in web-design projects
- Screenshots from videos I watched (YouTube, Dailymotion, etc)
- Videos/movies I downloaded from the web
Audio files
It'd also be easy for the hacker to track what audio files I was listening to on various websites. The recovered items included:
- Songs
- Podcasts
- Voice recordings
- etc
Documents
Even though document files don't seem to be directly connected to browsing history, but there are two important points to mention in this regard:
- Many users open documents, such as, PDF files, in their browsers ( I often do)
- It's good to know that file recovery tools may restore confidential financial and private document, such as, deleted business plans, financial reports, medical records, etc, as part of the recovery process.
If you handled such documents on the web, the recovered docs can be directly linked to your online activities. In my case the recovered documents included:
- Financial plans
- A password list
- Email headers from my Gmail inbox
- Task titles from my Asana profile
- Article drafts
- Powerpoint presentations on company projects
Note: While discussing the privacy concerns of document recovery, it's also vital to acknowledge how efficiently managing these documents can streamline your workflow. Effective organization of your digital files not only secures them but also saves considerable time and resources. For those looking to enhance their document handling processes, exploring examples of personal document management software can be very helpful. These tools are designed to make managing your files easier and more efficient, contributing to a smoother and more organized digital environment.
How to permanently remove your browsing history?
So now you must be wondering: How do I securely and permanently remove my browsing history if my browser can't guarantee that? Here is the answer.
To securely and permanently remove your browsing history, you need to use a privacy software. These tools are designed to seek out and overwrite the confidential information contained in your history files with random characters so even if the files are restored, the original information is gone from them.
After a secure overwriting, even if the guy opens the same file that previously contained the photo of a Playboy girl, or a site URL, now all he can find is a bunch of nonsense characters in the file. Something like this:
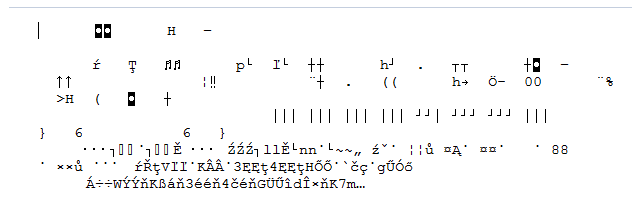
If you wipe your browsing history daily, after you finished using your computer, you can make sure that your confidential activity traces can't be recovered by unauthorized parties. And it's not at all rocket science to wipe your history. Just follow the few easy steps described in this guide and you won't need to worry about your browsing privacy anymore!
In conclusion, it's clear that even after clearing your browsing history, your sensitive data can still be at risk. But there's a straightforward solution to ensure your online activities remain confidential. Consider using east-tec Eraser, a powerful privacy software designed to securely and permanently remove your browsing history. By overwriting confidential information with random characters, it leaves no trace for unauthorized parties to recover. It's an effective way to protect your browsing privacy, ensuring that your confidential activity traces remain out of reach. Download east-tec Eraser and ensure your confidential data remains secure.

